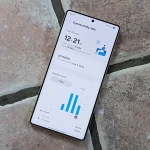
Unlocking Samsung’s Hidden Wi-Fi Features: A Deep Dive into Connectivity Labs
Samsung Galaxy devices are renowned for their rich feature sets, but some of the most powerful tools remain hidden beneath the surface. One such gem is Connectivity Labs, a concealed...